The October 2019 ASPECT conference was by and for signaling engineers and was organized by the Institute of Railway System Engineers (IRSE). Surprisingly though, the topic chosen for the opening session was not Positive Train Control, ERTMS or CBTC improvement. The topic was cybersecurity.
The opening session was ‘Oh, cyber security doesn’t affect me … right? Integration and cyber security’ by Colin Hamilton-Williams, of SNC-Lavalin Atkins. Throughout the conference, this title indeed summarized the sentiment of the audience. Conversations with stakeholders at the event confirmed that while cybersecurity was of great concern, these stakeholders lacked answers to the why, what and when of addressing the problem, and that there was a widespread perception that cybersecurity was little more than encryption.
Why: safety and reliability of operations
The why of cybersecurity is simple. Without security, the rail system can be neither reliable nor safe. The continuing trend towards increased connectivity is steadily increasing cyber attack opportunities targeting vital networks, which are the control networks responsible for safe and reliable operations. While many vendors, service providers and operators are ‘designing in’ protection for personally identifiable and corporate-confidential information, far fewer enterprises are designing robust cybersecurity measures for safety-critical and reliability-critical networks. This urgently needs to change.
The business imperatives for continued increases in connectivity will not change any time soon. Examples of connectivity drivers include:
- Transportation authorities and other government agencies demanding safety and other reports,
- Central enterprise security monitoring systems extending visibility into vital networks,
- Cell phone apps and station signage needing automatic updates of locomotive locations and schedules,
- Track repair teams needing accurate reports of, and control over, which tracks are out of service, and
- Predictive maintenance applications needing detailed information about equipment usage to purchase replacement parts and schedule maintenance crews optimally.
Connectivity is essential to modern, efficient operations, but must not put safe or reliable operations at risk. Cyber security standards, such as IEC 62443 and the draft CENELEC TS-50701, provide guidance as to how to manage connectivity risks. The guidance however is complex, and it is difficult to work out the difference between security designs that are currently acceptable, versus those that will stand the test of time.
What: first protect vital networks from external attacks
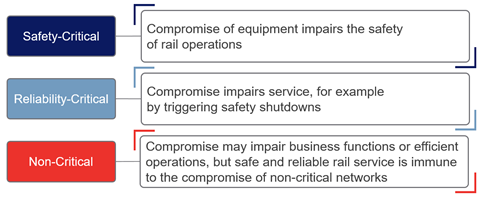
The IEC 62443 standard is focused on automation and describes four levels of network and system criticality. The upcoming CENELEC TS-50701, still in draft state, suggests five level of criticality. The extra level in 50701 is because, the standard argues, rail networks are more complex than conventional automation networks. Complexity is the enemy of security. While these standards make a case for greater granularity, a first step towards understanding and applying the standards is to start with only three level of criticality: Non-critical (IT systems), Reliability Critical and Safety Critical systems. In rail environments, these last two types of networks are often referred as vital networks.
As 62443 and the draft 50701 point out, IT-centric security solution does not work well to protect vital networks. IT solutions focus on protecting data, not protecting safety and reliability. In both 62443 and 50701, the protection of vital networks starts with segmentation, which means restricting the flow of information between network zones, not merely encrypting those information flows. Monitoring, encryption, and other security practices are also important, but the first technical step after agreeing to a new cybersecurity plan is always to correctly segment vital networks.
When segmenting these networks, three simple principles and practices lead to robust, practical and ‘future-proof’ designs:
- Manage all vital networks as ‘security-critical’ networks.
- Regard all information flows from non-critical to critical networks as potential attacks.
- Control those information flows, preferably physically, since over the course of time, all software will be found to have defects and security vulnerabilities.
These principles lead to a future-proof design because all cyber attacks are and will always be information - this is the very definition of ‘cyber.’ A comprehensive inventory of all incoming information flows, including both offline and online flows, is also a comprehensive inventory of all possible cyber attack vectors. Control all those vectors physically, and we are immune to cyber attacks.
That said, we must recognize that these principles represent an ideal and that we should design our systems to come as close to this ideal as practical. Since the ideal can never be reached, there will always be a place in our security programs for security monitoring, intrusion detection, practiced incident response teams and regularly tested backups and recovery systems. But - we must never confuse detection, response, and recovery with prevention. To protect safe and reliable operations, our first priority must always be preventing cyber attacks and their consequences.
An essential tool for controlling information flows and preventing cyber attacks is unidirectional gateway technology, deployed at the perimeter of vital, security-critical networks. While firewalls are software, and over time all software has defects and vulnerabilities, unidirectional gateways are a combination of hardware and software. The hardware is physically able to send information in only one direction - from a critical network to a non-critical network, while the software replicates servers and emulates devices, enabling straightforward access to vital network data. In short, unidirectional gateways provide external networks with access to vital network data, without providing external attackers with access to vital systems.
The strength of unidirectional gateway technology is recognized in both IEC 62443 and the draft TS-50701 standards. The only way that a vital network can transition from an uncompromised to a compromised state is if attack information enters the network, through either offline or online means. Connectivity risks are all online risks, hence the focus in the standards on segmentation using unidirectional protections. Unidirectional technology provides ‘future proof’ protection from online attacks originating on external networks. No matter how sophisticated online attacks become in the decades ahead, cyber attacks will always be information - physically block those attack information flows, and we have eliminated the risk of online attacks.
Example: Passenger Rail
What does this mean in practice? A (very much) simplified network diagram for a passenger rail control center is illustrated below. Firewalls may be used extensively both inside and outside security-critical networks, but only unidirectional gateways are permitted at the boundary between critical and non-critical networks.
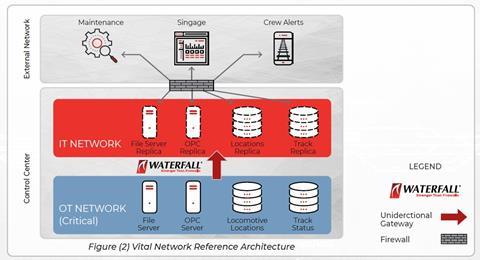
In the example, the gateways replicate four servers from the security-critical operations network to the external IT network:
- A SQL Server database is updated once per second with current locomotive locations - the replica database on the IT network is used to update passenger cell phone apps (not illustrated) and station signage.
- A SQL Server database stores information about track outages for maintenance - the replica database updates maintenance crews and provides them with positive control over how long tracks that they are repairing are out of service.
- An OPC server stores information about how long and how intensely track, switching, rolling stock and other equipment is used - the replica provides this data to enterprise predictive maintenance applications.
In addition to the protection from online attacks due to network connectivity, which are the focus of this article, robust protection for vital networks demands control over offline information and attack flows as well. In Figure (2) the unidirectional gateway also replicates a file server from the operations network to the IT network. Technicians and engineers on the operations network can simply ‘drag and drop’ files into this file server, and the gateway automatically transfers those files through unidirectional hardware to the IT replica file server. This simple mechanism dramatically reduces the need to use removable media on security-critical networks.

When: future proof rail infrastructure now
The cyber threat environment continues to worsen. Attack tools and attack techniques continue to become more powerful. Today’s ‘nation-state-grade’ attacks will be tomorrow’s pervasive threat - the tools of organized crime. Any security program that fails to take these realities into account is doomed to fail.
Upcoming government requirements, such as the NIS directive in Europe, will change from country to country. In many cases, rail systems will be labeled by governments as critical infrastructures, and operators will be required to dramatically increase the resilience of their systems to sophisticated cyber attacks.
Robust, future-proof, physical and unidirectional control over essential data flows is straightforward and practical. Better yet, such designs substantially simplify some of the most costly parts of software-based security programs. For example, security updates and patches are very costly to apply to vital networks, because of the risk of safety-critical and reliability-critical malfunctions in the new software versions. In a unidirectionally-protected vital network, operating systems and software can be updated at a deliberate and cost-effective pace. This is in contrast with costly emergency updates needed for the most serious vulnerabilities in vital networks that are protected by software alone.
Rail system operators cannot afford to get security wrong and, bluntly, have better things to do than be dealing with security crises for the next few decades. Simple and cost-effective principles and practices, such as unidirectional gateway technology between critical and non-critical networks, are sufficient to produce robust network designs, providing physical protection from both today’s and tomorrow’s most sophisticated cyber threats.
For more information on this approach to robust security designs, please download Waterfall’s latest eBook on this topic at https://hubs.ly/H0sqWcV0