
When I was chatting recently with the CSO of a large US metro system, he declared to me half-jokingly, “My operational system will be air-gapped for as long as they let me.” “They” in this case meant the organization’s IT departments who had been pressuring operations to implement digital transformation projects, in part to satisfy external partners who were requesting live data. That comment sparked this article: in today’s threat environment, air-gapped control systems are not immune to cyberattacks. Even more surprisingly, there is a widely-used approach to cybersecurity that both enables online digital efficiencies and provides stronger security than does an air gap.
How? Let’s start at the beginning: rails enterprises are universally seeking to improve operational efficiencies through increased automation and digital connectivity. The problem is that such connectivity poses a serious cyber threat to the reliable operations of railway systems and even to safe operations in many cases. How can we enable these digital efficiencies without putting our entire system at risk of crippling cyber attacks? At Waterfall Security Solutions, we work with the world’s most secure industrial sites, including many rail system operators and infrastructure owners, and we observe that the most common cybersecurity questions have straightforward answers.
In the industry, we see that most rails control systems are in one of three states: many are still offline/air-gapped environments, while others are connected to IT and external networks with firewalls, and still others are new builds designed for greenfield environments. In this article I will explore how to enable digital transformation in air-gapped systems without sacrificing the reason that these system are still air-gapped in the first place: protecting the resiliency of vital operations networks and safety systems against external cyber attacks.
FIRST STEP: IMPROVING INFORMATION FLOW
What is poorly understood in many enterprises is that even air-gapped systems have become vulnerable to very damaging cyber attacks. This exposure is because information exchange is essential to realizing most of the benefits of digital efficiencies, such as automatic ordering of spare parts, automatic scheduling of work crews, automatic updating of timetables and automatic notification to freight customers of the status of their shipments. In an air-gapped rail system, there is no way to do automatic or online transfer of the data needed to enable these efficiencies. This means that data must be transferred manually, most often via USB drives. Manual data transfer is inefficient and error prone. Worse, carrying USB drives or other media or laptops routinely between vital networks and IT networks risks introducing malware to the vital networks on these devices and media.
Firewalls are of limited help here – firewalls enable connectivity but increase cybersecurity threats, unacceptably. This is because every path through a firewall that lets data out of protected vital networks also lets attacks back in. This is true even when connections through firewalls originate in Operations Control Center (OCC) networks with destinations in IT networks. Once any firewalled connection is established, all such connections are bi-directional, potentially allowing attack information back into protected networks. Worse, firewalls are software. All software has defects, both discovered and undiscovered, and some of these defects are security vulnerabilities. For evidence of this, visit any firewall vendor’s website and see how many security updates were issued, and how recently.
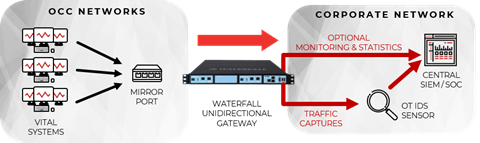
The robust solution to this problem is a Unidirectional Security Gateway. Unidirectional Gateways are a combination of hardware and software. The hardware is physically able to send information in only one direction - from the OCC network to the IT network. All cyber attacks are information. If no information can get back into the OCC network through the gateway, then no attacks can get back either. It does not matter how sophisticated the attacks are, or how many vulnerabilities are found in different pieces of software, the unidirectional hardware physically prevents any information or attacks from flowing back into the OCC network.
Unidirectional Gateway software makes copies of servers. The first server copied in most rails networks is a file server, to eliminate almost all uses of USB drives. Users or applications on the OCC network can drag-and-drop or otherwise transfer files to an operations file server. The Unidirectional Gateway automatically copies all such files from that server through the unidirectional hardware to an identical file server deployed on the IT network. Now operations information ranging from equipment usage statistics to locomotive locations and track outages can be communicated safely and automatically to IT users and applications, without ever carrying a USB drive into the OCC network, and without suffering the vulnerabilities that IT/OT firewalls introduce.
In a unidirectionally-protected network, there is generally still a very small amount of information that must enter vital networks, such as new anti-virus signatures, software configurations or even new software versions. This data is still carried into the network on portable media, but such transfers are rare and media cleansing stations can be deployed to sanitize the incoming data. Unidirectional Gateways dramatically reduce the exchange of media and laptops between OCC and external networks, as well as providing air-gap-class protections for the OCC.
NEXT STEP: ADDING MONITORING AND ASSET MANAGEMENT
Improved security monitoring is often the next step towards digital operations and modern security. OCC and other rails networks are operations-critical or safety-critical, and so should be monitored very closely. This creates opportunities to catch performance problems, insider attacks and other issues as early as possible.
To this end, modern rails enterprises generally add mirror port emulation software to their Unidirectional Security Gateway deployments. Mirror port replication supports the needs of the new breed of OT IDS sensors. The Unidirectional Gateway connects a mirror port on a managed OCC switch on one side to an OT Intrusion Detection System on the IT network.
With this unidirectional protection in place:
- OT IDS sensors can safely be deployed on IT networks, where those devices are most easily managed by Security Operations Center (SOC) analysts,
- Leading OT IDS security products, such as those from Nozomi, Dragos, CyberX, FireEye, Cylus and other Waterfall partners, all inspect OCC network traffic and report suspicious anomalies to the SOC,
- Rails enterprises can be completely confident that no attack from the IT network or the Internet can pivot through the OT IDS sensor back into the OCC switch to put rails operations at risk, and
- A key function of these modern OT sensors is asset management - OT IDS technology not only detects intrusions and other anomalies, the technology can build up a picture of the OCC network and of the state of all of the cyber assets on that network.
Security monitoring is vital to safe and secure operations - after all, we can only optimize what we measure. We must measure our security to ensure that it is at the level we need. Furthermore, we can only protect from cyber attacks that equipment which we know we have. A current cyber asset inventory is an important input into any rails’ cybersecurity program. In short, OT IDS sensors provide important visibility into OCC networks, and Waterfall’s Unidirectional Gateways enable safe deployment of those sensors.
ADDITIONAL EFFICIENCIES
Enterprises who have enabled safe, secure, and robust unidirectional digitalization generally deploy additional unidirectional software replications over time on their existing Unidirectional Security Gateway hardware. SQL Servers replicated to IT networks for example, can serve locomotive location information to websites and passenger cell phone apps. OPC servers can provide equipment usage information directly to maintenance planning modules in Enterprise Resource Planning Systems. A Remote Screen View server can enable “look but don’t touch” remote support services for product vendors and service providers.
Waterfall is also asked regularly about “greenfield” systems that are currently under construction. How can these systems be designed to maximize the benefits of modern digital efficiencies and do so safely? The short answer is to design unidirectional protections into OCC, Signalling, Electric System and other vital networks from the start. Unidirectional Security Gateways replicate or emulate vital systems to IT networks. The replicas allow IT users and applications to profit from access to operations data, without ever accessing vital systems in ways that put those systems at risk.
FUTURE-PROOF SECURITY
All cyber attacks are information - this is the meaning of “cyber.” This will never change. Unidirectional Security Gateways enable digital information to flow unidirectionally, without permitting any “backflow” of potential attack information into vital networks. These hardware-enforced, physical protections for OCC networks defeat both todays cyber/information attacks as well as tomorrow’s, no matter how sophisticated those attacks might become.
For more detail on this vision for safe and secure digitalization and rail systems efficiencies, download the latest Waterfall eBook: Cybersecurity Imperatives For Vital Rail Networks At Operations Control Centers.

















